As of this month, I’ve moved to Arch Linux as to my day-to-day operating system. That’s my 4th attempt so far, but I’m taking it seriously from this moment.
Exploration
Arch by the way is a big FOSS1 project, and with that come all the mass collaboration benefits of big FOSS projects: forums, wikis, open docs, etc.
Speaking of Arch by the way, the official website is featuring very based and abundant wiki where you can find pretty much anything from “how to install arch” to “yubikey use cases”.
Not gonna lie, it accidentally happens that some package gets broken, making the way out very unclear (my windows dualboot has just gotten damaged, that’s for good though). Usually, 5-10 minutes on the web are enough to fix everything and get some additional knowledge about the OS in the meanwhile. Though it is generally a good idea not to overbloat the system with poorly maintained packages and dependencies (packages from official repositories are more than enough for an experienced user).
Threats
The main problem with today’s “normie operating systems” is that no one except their devs knows exactly what code the OS is running. That means one has no choice but to trust Microsoft & Apple & Google & Yandex & Chinese Communist Party that spooky processes don’t have backdoors, hidden parts and are not being used to spy on them. I personally don’t mind if any data from my camera roll gets compromised, but there are things I prefer to stay private or cannot afford losing (i.e. civil documents, keys to my crypto wallets, PGP master key). Therefore, data leakage is considered a threat. It may come true due to user error (I won’t talk about that one seriously) or due to targeted attacks. A general solution would be to use some Linux or BSD distro that is open source (which is ez to say, but hard to actually implement). Although it does not fully mitigate the risk, I would rather rely on transparent projects’ reputations than on ones of Big Tech corps.
Apart from having a suspicious operating system, every modern PC has various management modules physically attached to the motherboard as well as some BIOS/UEFI firmware installed there by default. These modules are constantly listening to external commands as long as the battery is attached. Not to mention, they run proprietary code (that we can only guess upon) which makes it technically possible that the data is compromised even when you use a FOSS operating system. People usually overcome this threat completely by corebooting their PCs so that none of the proprietary firmware can be possibly run.
Physical tampering evil maid attack - when an attacker, having physical access to the PC, modifies some system components (alters EFI partition, mounts a keylogger, swaps the entire hardware) with the sole purpose of touching a passcode and later applying it to the encrypted disk. if the disk is unencrypted, it is trivial to read/copy the contents. Be aware, don’t make H. Biden’s mistakes
Compromised channel with malicious listeners (non-network MITM: power analysis, optical, acoustic, thermal, etc) - uncommon, very hard to implement, yet powerful way to sniff someone’s keys. If you find yourself wiretapped with such precision - my condolencies...
Safety
I’m not planning to disassemble my laptop and verify every component with magnifier and tweezer in the nearest future, however I’ve performed some but not all safety actions to make my data secure from a stranger’s eye. Once again, it is not about the fact that the data is compromised, it is about the risk of undetected leakage that I refuse to accept.
It’s easy to blame some hacker who sits in his room and finds a way to pull your data, but it’s statistically not a fraud who ends up with an empty crypto wallet.
So now I have...
| LVM on LUKS -encrypted NVMe SSD partition | |
|---|---|
| OS | Arch Linux |
| bootloader | GRUB 2.12 |
| display manager | ly |
| window manager | hyprland on wayland |
| shell | bash |
| terminal | alacritty |
| file manager | lf |
| app launcher | tofi |
| text editor | nvim by nvchad |
I don’t use a DE (desktop environment) cuz it stands away from simple .dotfiles2 philosophy that Linux is famous for, plus I’m catching some cringy Windows Registry vibes with dconf database .

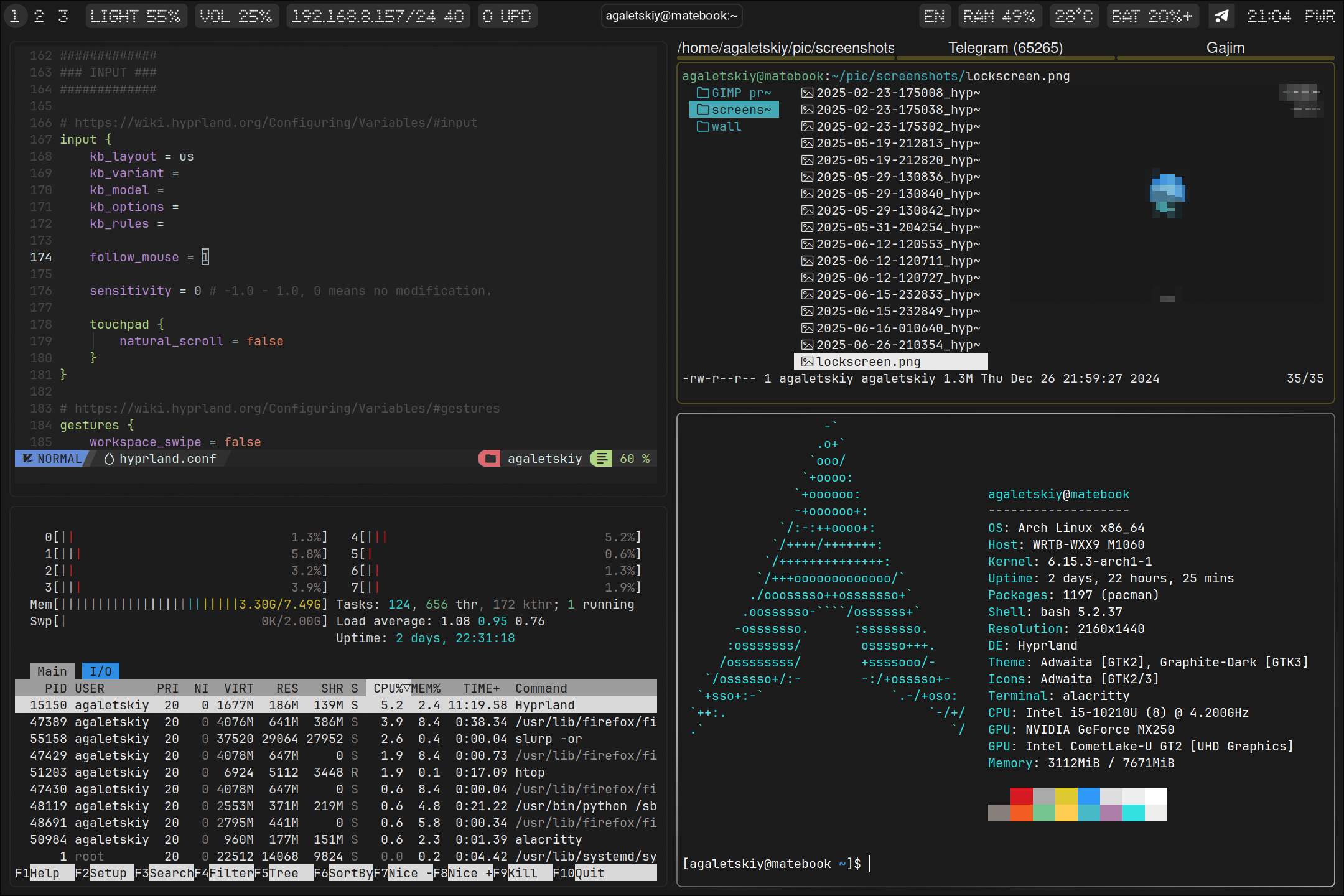
The theme is custom and pretty basic. Once I get everything ordered and polished here, I may publish my dotfiles. If you need anything specific - feel free to DM me.
ToDo
- Enroll my passkey device to LUKS volume
- Encrypt boot partition to counter evil maid - it will slow down boot process a lot, I’m not quite sure I want that rn
- Secure boot
- Try plain dm-crypt (detached LUKS header) - to make the thing indistinguishable from a disk filled with random data. Deniable encryption y’know...
Footnotes
Free and Open Source Software - software that has been made public. It still comes with a license that grants or doesn’t grant a right to modify/share/monetize the code. Licensing is essential cuz if the software does not come with a license, it can quickly obtain one by a first person to notice it and claim the ownership. I’m intentionally oversimplifying the process, but you get the idea. ↩︎
Dotfiles usually stand for files in
~/.configand~/.localdirectories. They’re meant to store user-specific configuration parameters and to be synchronized between various hosts. ↩︎